Innovation is the key to so many success stories. From the earliest fossil record showing crude tools made of stone, to the 21st century CEO picking up an iPad and calling it a business expense. Innovators find ways to get the job done better than the men before them.
This idea comes to mind more than ever while the 2012 Consumer Electronics Show takes place. Already there have been announcements made about how company’s like RIM, Intel, and Microsoft will be addressing the future. New pieces of hardware and software will be coming out, and plenty of media attention is indicating that anyone not riding the wave of the future, will be swept away and forgotten.
That’s when it’s a good idea to take a step back. Take a deep breath. Shake your head a bit, and consider the following question: How do these new technologies benefit my business?
The term “Early Adopter” was coined by a very smart man named Everett M. Rogers. In his book “Diffusion of Innovations” he was able to describe what he called the five stages of the adoption process.
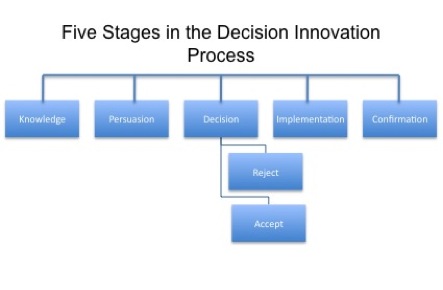
Knowledge: The point where you are made aware of a new technology or innovation. At this point, you know little about it besides the fact that it exists. It is the billboard on the highway declaring all your problems solved.
Persuasion: The process of gathering information about this new wonder. This is where having a professional voice to assist you is invaluable. They can help you to examine your company’s needs, and answer the appropriate questions. What results can you expect from this innovation? What will it take to implement it? Is it a necessary adoption for my business to run competitively?
The Decision: Pretty straightforward. Yes or no, and it all comes down to you, the boss. Ultimately, you (or the shareholders you are representing) decide what is best for the future of your company.
Implementation: Here again is where you will need to rely on your team to get things done smoothly and efficiently. Whether it’s a new printer in the lobby, or a chain wide user interface update, you want to keep the business up and running. New training may need to take place. Schedules may need to be adjusted to allow for maintenance. These sorts of things will need to be communicated clearly to all involved. You also don’t want to destroy what was working before. In the case of a large scale change, you may wish to update only small pieces at a time, and evaluate the results as you go.
Confirmation: At the fifth and final stage, you conclude your decision. Is this innovation right for you? If yes, then congratulations! Your business will run better with this latest enhancement. If no, then congratulations! You can continue to run your business successfully without it. Time to move on.
So where does your IT department fit into this?
If you were to ask them, they might tell you to include them in all 5 steps. I would encourage you to include them in at least 3, if not 4 of these steps.
- Step 1: Knowledge – Your team should keep you up to date on the latest and greatest.
- Step 2: Persuasion – Your team should keep themselves up to date on the latest and greatest.
- Step 4: Implementation – Your team should have a keen understanding of how best to implement the innovation.
- Step 5: Confirmation – Your team should be a great source of information for you as you make your final decision.
It can be a little daunting to make a decision regarding technology in the business world, especially when things seem to change so quickly. With the right team at your back however, you can make the right decisions that much easier, and find yourself at the head of the pack.